Maintaining an organizations data is critical in today’s technology driven world. Malicious entities know this best and have set the stage for the new field of cybersecurity that is paramount to your success. According to TechTerms, “Data is processed and stored information… in the form of text documents, images, audio clips, software programs, or other types of data.”
This information at its basic form is comprised of “ones and zeros, known as binary data” that can be transferred using network connections. The importance of data is not represented in this definition. Data can be seen overall as a comprehensive and economic asset that is the lifeblood of most organizations.
Given how critical this information is to the day to day functions of organizations, it’s obvious why so many cyberattacks target this digital treasure trove of a company’s data. New vulnerabilities pop up daily that put organizations at risk. I’d like to talk a little more about this cyber risk and the need for a cybersecurity assessment. Let’s first start by understanding that an organization’s network can be exposed to risk from internal and external sources.
Internal Cybersecurity Risks
An organization’s network can actually be more vulnerable from the inside than the outside. Although an organization may take measures to effectively screen and qualify its employees, no measure ensures 100% safety. Disgruntled or malicious employees can wreak havoc on an organization’s network. Additionally, some employees can unintentionally access and release confidential information or even release a virus into the organization’s network.

It is quite common to witness hackers taking advantage of weak internal security. A hacker can enter a corporate network because they performed some social engineering that provided an entry point for the hacker from an unassuming employee. Also, if a hacker does find a way through the external perimeter defense, the attacker can take advantage of a soft internal security posture to proliferate any attack that they desire. Employees have been known to accidentally access information that has been deemed confidential.
Security measures such as password policies and administrative rights will need to be studied carefully. Viruses in the past few years have caused tremendous failures of networks and systems while preventing access and destroying information. These issues can cripple an organization’s ability to function. The most common cyber threats today are malware (ransomware, spyware, spam, etc.) that is unknowingly downloaded by employees to the network, and then it proliferates making computers unusable and allowing access to information on the network that the company does not want to make available.
Email and access to email has also proven to be an easy entry point for hackers. Much care needs to be taken when providing email access internally and externally these days. It is easy to flood a network with malicious emails that cause a wide variety of problems.
External Cybersecurity Risks
Externally, hackers are constantly coming up with new tools, tactics, and techniques for invading an organization’s network. Even if an organization has not made major changes in its infrastructure, hackers have effectively exploited some of the more sophisticated security schemes deployed at organizations. We live in a perfect storm where hackers have the time, easy access to resources and expertise on their side.
Many times hackers may not be as obvious about their attacks on an organization’s network. Instead of infecting it with a virus or bringing it down; they may use it as a relay site, a place to store information that may be inappropriate, or simply gather proprietary company information through tools such as spyware and keystroke loggers.
Internal changes also open the door for external security risks. A simple configuration change may be necessary for the system to function properly but it may have left vulnerabilities in the network. On the other hand, something may have been improperly configured leaving vulnerabilities as well. Whatever the case, when an organization loses access or control of their data; operations come to a halt, airplanes stay grounded, payroll goes unpaid, client information is jeopardized, and storefronts are closed. The implications are limitless.
The amount of data being kept electronically and the need to both securely access and share that data has made cybersecurity paramount to the success of businesses today. It cannot be stated enough that protecting your data is critical. The first step in securing an organization’s data is to and eliminating known vulnerabilities is to perform a comprehensive cybersecurity risk assessment.

The Cybersecurity Risk Assessment
In preparation to assess a cybersecurity risk, a scope must be defined. Depending on the size of the organization’s network, it may be necessary to break up the assessment into sections such as; locations, departments, applications, subnets, and so on. All involved parties must clearly understand the terminology used in risk assessments. We like to start by reviewing the National Institute of Standards and Technology (NIST) with our partners and focusing on two important risk management frameworks: the NIST SP 800-37 and the ISO/IEC27001.
To create a comprehensive network inventory, we begin by completing a thorough network discovery and asset identification review. Since hackers will exploit virtually anything, we must review the critical and noncritical hardware pieces. This is necessary as a known process is to locate the innocuous assets and use them to gain access to the critical assets. A that point, you may then create an entire network diagram to provide a simple visualization and documentation of your entire network. The diagram below is a common layout of the IT environment of organizations today.
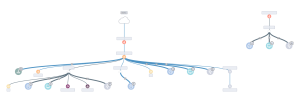
Identifying Threats
Once all assets are identified, the process of identifying threats can begin. The threats our forensic and cybersecurity experts identify are derived by understanding the common tactics and techniques that hackers use to take advantage of networks. After assets have been diagnosed with a vulnerability, reports are created about the possible repercussions should that vulnerability be exploited. The following steps include analyzing the impact of discovered risk, determining the likelihood of exploitation, prioritizing mitigation recommendations by asset, and creating a detailed report that contains all findings and recommendations.
Performing a cybersecurity risk assessment can be a daunting endeavor to undertake. Taking these proactive cybersecurity steps can provide peace of mind and shows both clients and internal staff that you are serious and conscious about keeping your information safe and secure. Many organizations inquire about the best time to begin a cybersecurity assessment, however, we always recommend as soon as possible.
Your Partner in Cybersecurity
If you are looking for a resource to help begin the process of a cybersecurity assessment, we have an entire team of experienced cybersecurity experts available to simplify this process. Clear Winds state-of-the-art techniques such as internal and external penetration testing, network discovery, and risk assessment tools make it easy to incorporate a new layer of cybersecurity defense.
With over twenty years of security-specific experience, Clear Winds is well qualified to offer a wide variety of cybersecurity services. Our consultants have extensive experience in designing, implementing, troubleshooting, and auditing complex networks and security infrastructures. In addition, they hold appropriate security certifications including Cisco, Check Point, and CISSP. Clear Winds uses a holistic assessment methodology to ensure that every element of security is studied. Our methodology encompasses governmental regulations, business, administrative, physical, and technical concerns.
This methodology is designed to be flexible in nature so that it can be tailored to meet an organization’s specific requirements during the process. Clear Winds’ toolbox is prepared to support a wide array of requirements. For additional information on cybersecurity, visit Clear Winds Technologies cybersecurity resources at https://www.clearwinds.net/cybersecurity/.